You planned a marketing campaign.
You sent content to all the email addresses in your database.
Open rates dropped, a few people wanted to unsubscribe, some didn’t respond at all.
But someone, one of those silent ones…
Marked it as spam.
And maybe complained about you to the Ministry of Trade, KVKK or İYS.
From that moment on, your brand may be in danger.

📌 In today’s world, email is not just a means of communication, it’s also a legal responsibility
Who you communicate with, why, and how should now be recorded.
In this article, we will explain how unauthorized email sending can be devastating for your brand; legal risks, invisible damages and how you can protect yourself with the Consent, Cookie and Privacy Compliance Management Model that eliminates this risk.
İçindekiler
ToggleThe Era of “We Got the Data, Let’s Send It” is Over
In the past, every e-mail address received at a fair, in a form or on a website would be included in the “marketing list”.
Agencies or internal teams would upload those lists and send campaigns to all data.
Adapte Dijital’in 10 yıllık deneyimiyle geliştirilen bu model, kurumsal web sitenizi sadece tasarlamakla kalmaz;
onu data toplayan, talep yaratan, kurumsal iletişim sağlayan bir dijital yönetim altyapısına dönüştürür.
Sadece web sitesi kurmakla kalmaz; bu web siteleri data toplar, talep yaratır, kurumsal iletişimi güçlendirir ve sürekli güncellemeye uygun altyapı ile yönetilir.
But this process is no longer legal.
And these boundaries are becoming clearer with each passing year.
Now communication can only be established if there is consent
According to the KVKK, explicit consent is required to send a commercial message (e-mail, SMS, phone) to a person.
The Ministry of Trade also requires recording this process through the İYS (Message Management System).
This means:
- You may have been given the email address
- But for what purpose,
- For which content it was approved,
- When it was received,
- Where it is stored…
Each of these is important.
Otherwise, every email you send could turn into a potential penalty file.
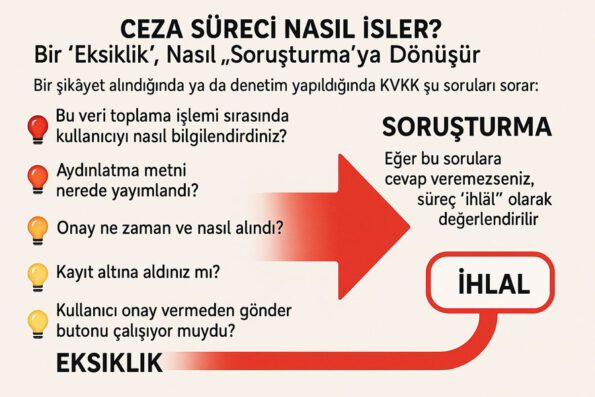
Why Is It So Serious? It’s Not Just “Disturbing”
An email sent to a person without their consent is no longer just “annoying”, but a legal crime.
What happens when a complaint is made?
- The user complains about you via the IYS
- The address you send to is analyzed based on IP, date, content and the system
- KVKK or the Ministry of Trade requests open consent from your system
- If you cannot show it, the penalty process begins
And this penalty process is not only financial:
- You will be blacklisted
- Email providers mark you as spam
- Platforms like Gmail and Outlook impose quotas on you
- Your mail system may shut down
- Your domain name is at risk
- Your brand trust is damaged
So with just one email you won’t be “campaign ineffective”, you may also lose your reputation.
Blacklist Truth: Once You Fall, It’s Hard to Get Back
Being blacklisted in mail systems is like being invisible in the digital world.
No e-mail address can reach your inbox, and every message you send is caught in the spam filter.
Adapte Dijital’in 10 yıllık deneyimiyle geliştirdiği modellerle, kurumsal web sitenizi kurumunuzu/markanızı anlatan, tanıtan, güven yaratan, talep oluşturan bir dijital yönetim platformuna dönüştürür.
Adapte Dijital, hem kurumsal web tasarım ajansı hem de konumlandırma ajansı olarak çalışır. Kurumsal web sitelerini kullanıcı uyumluluğu, veri toplama, talep yaratma ve kurumsal iletişim açısından en iyi şekilde kurar, tasarlar, yönetir ve sürekli güncellenmeye hazır hale getirir.
Why is a blacklist created?
- Email recipients mark it as “spam”
- A large number of bounces (unreachable addresses)
- A sudden increase in sending frequency
- Sending with lists that do not have permission records
These signals can blacklist you from:
- Gmail
- Outlook
- Yandex
- Zoho
- Mailing tools like Mailchimp, Sendinblue
- DNSBL (global spam lists)
📌 Once you’re on these lists, it can take months to get out.
📉 And in the meantime, your email channel will be unavailable.
The Collapse of Institutional Trust: Being a Spammer in the Eyes of the User
Let’s take a look at the user side.
The visitor filled out a form.
It said “For communication”.
But then product promotions, campaign messages, sales e-mails started to arrive.
The user thinks this:
“These people are using my data without permission.
It’s not trustworthy.
I feel bad.”
Users are now paying attention not only to content, but also to how you treat data.
And this perception can lead to your brand:
- Comments on social media
- Score on complaint sites
- Google reviews
- Recommendation rates
It is directly reflected.
“Unauthorized communication = lack of trust”
That’s why every email sent without permission not only damages the campaign but also the brand.
What Does Permissioned Data Mean? How to Get Real Consent?
One of the most critical concepts in email marketing is now: Permissioned data.
No matter how big your email list is, if you haven’t received explicit and recorded consent from the people on that list, that list is not legal.
What is real consent?
According to the KVKK and the Ministry of Trade, in order for you to use a person’s contact information:
- It must be clearly stated what it will be used for
- Information must have been provided
- The consent was given with free will should be
- Must be recorded
So just “they filled out the form, the email came” is not enough.
📌 Explicit consent; must be received with the content, timestamp and user approval.
“Subscribe to the newsletter”
“I want to be informed about campaigns”
“I accept to be contacted”
Such options should be provided and recorded by the system.
To make your website legal and reliable, we have developed You can review our Consent, Cookie and Privacy Compliance Management Model.
If Consent is Obtained, Where Is It Stored? Why is the Logging Process Necessary?
If you have received explicit consent, that’s great.
But can you show that consent?
These questions come up in audits:
- When did you receive consent from this person?
- What content was it taken from?
- Which IP and device did it come from?
- Which information text was shown at that time?
If you do not systematically store this information, consent is not considered valid.
Therefore, every organization that does email marketing should have an infrastructure that can log consent records.
What should be in the log system?
- User’s email address
- Content text approved
- Time to check the consent box
- IP address
- Device information
- On which page it is given
These records are the only evidence that protects you in the event of a possible complaint.
To see the effect of a compatible system on a site, take a look at our Motto Plus example.
CMS, CRM, Mailing System: How to Achieve Triple Harmony?
Getting the data right is good.
But when systems don’t know each other, it leads to great confusion.
For this reason, triple technical harmony is a must in marketing processes:
1. IYS (Message Management System)
- It is the national system where the official records of commercial electronic message permissions are kept.
- The records here are official evidence.
- Everyone who will send e-mails and SMS must be integrated into this system.
2. CRM (Data Management System)
- It is the main source where user information, campaign history, and marketing actions are kept.
- Only authorized people should be transferred to CRM.
3. Mailing Tools (Mailchimp, Sendinblue, etc.)
- They are tools that run email campaigns.
- They only accept permitted data to avoid being blacklisted.
- Lists without checkboxes are removed from the system.
📌 The fact that these three structures are not integrated with each other may cause breakage and penalties.
How Does Our Model Build This Triple System?
The Consent, Cookie, and Privacy Compliance Management Model works not only with legal texts but also with technical systems.
The stages work as follows:
1. Website Consent Infrastructure is Established
Information texts, open consent boxes and preferences are added to all forms.
The form cannot be sent without user approval.
2. Logging System is Activated
Each approval is recorded with date, IP and content information.
If necessary, this data can be exported and submitted for auditing.
3. IYS Integration is Provided
Each user you will send commercial messages to is registered in the IYS system.
If necessary, your internal database is synchronized with IYS.
4. CRM is Cleaned and Edited
All user data in the current CRM is reviewed.
A clean list is created by filtering only the approved ones.
5. Mailing System Adapted
Permitted data is transferred to the mailing system.
Rejected, complained or old data are left out.
6. Documentation and Training
The process is documented.
Teams are trained on how to maintain this system.
📌 In this way, a marketing infrastructure that is not only compatible but also sustainable and performance-oriented is established.
Conclusion: Every Email You Send Is Either a Message of Trust or a Message of Risk
Email marketing is a powerful tool.
But if it is not used correctly, it can become a threat to your brand.
Being a spammer in the eyes of the user is perceived not only as a “technical error” but also as a corporate posture problem.
That’s why our model:
- Protects you from legal risks
- Optimizes your marketing systems
- Enables you to establish trust-based communication with your users
- When an audit comes, it reveals everything with documents
Before – After: Not Only the System, But Also the Perception Changes
Before:
- Email lists that are not known who added them and where
- No boxes or text in forms
- Emails are sent without consent
- Documents cannot be provided when a complaint is received
- Mail systems are getting blacklisted
- Every post is a source of stress >
After (after applying the model):
- Explicit consent box + visible disclosure text on every form
- No data is included in the systems without approval
- User data is logged and recorded
- Complaint risk is reduced to zero thanks to IYS integration
- Marketing campaigns are not spam, they are trust messages
- The brand is now a respected actor in the e-mail box
📌 This transformation is not only done to “avoid penalties”, but also to gain digital trust.
To see the effect of the compatible system on the site, take a look at our Motto Plus example.
6 Basic Gains the Model Will Provide to Your Brand
The Consent, Cookie and Privacy Compliance Management Model is not just a technical solution, it is a corporate communication strategy.
Below, we summarize the 6 biggest benefits the model provides to businesses:
1. Legal Protection and Audit Assurance
All e-mail permissions, information, and log records are presented completely in KVKK and Ministry of Trade audits.
Every communication can be proven with documents within legal limits.
2. Permitted and Qualified Marketing Infrastructure
Your marketing teams only work with approved, targeted, and logged data.
Campaign conversion rates increase, and complaint rates decrease.
3. Cleanliness and Order in CRM and Mailing Integration
All scattered data systems become compatible.
Data quality increases, performance reports become meaningful.
4. Involvement in the Official Process with İYS
The corporate communication criteria expected by the Ministry of Trade are met.
Permitted message sending becomes sustainable.
5. Rebuilding User Trust
Users respect the institution with the feeling of “no communication without my permission”.
Incoming e-mails are perceived as useful information, not spam.
6. Strengthening Corporate Perception
You can now continue your email sending as a “corporate communication strategy” rather than a “marketing effort”.
Your content will be returned, and your lists will become valuable.

We have developed You can review our Consent, Cookie and Privacy Compliance Management Model.
A Real Life Example: Stronger Than Loss of Trust To the system
A software company faced a huge wave of complaints due to a campaign email it made in 2023.
Most of the people on the email list were collected from fairs years ago, and it was not known who received which permission.
The process started with a complaint:
- Mail server blacklisted
- 8,000-person database in CRM became unusable
- 120,000 TL fine imposed by the Ministry of Trade
- Mail system was closed for 2 weeks, campaign was canceled
What happened next?
Model implemented by working with Adapte Dijital:
- New data collection systems established
- Old list cleaned up and only allowed ones were left
- Website restructured
- Mailing systems securely integrated
- Conversion rates increased by 41% in 3 months
- New customer acquisition costs decreased by 22%
And most importantly:
The company now communicates not with data, but with trust.
Not Just Legal, But Ethical Stance: Institutionalism Starts Here
Every e-mail a business sends is a statement of “we are here” in the digital world.
But what is the intention, what is the system, what is the value behind this “we” statement is much more important now.
Every message sent without permission goes to the spam box, not to the brand
Users no longer focus solely on the content of the message, but also on the way it is sent.
That’s why the essence of our model is not just compliance:
it is respect, transparency and sustainable communication.
The result: Permissioned Data = Strong Brand
Today’s digital an unauthorized email in the world;
- A complaint,
- A penalty,
- A blacklist,
- A loss of reputation
could occur.
But not every email sent with authorized data message;
- A trust,
- A bond,
- A return,
- It becomes a brand value.
Adapte Dijital’nin İziz, Cookie and Privacy Compliance Management Model, you can move your business to the strong side of this difference.
To see the effect of the compliant system on the site, take a look at our Motto Plus example.
📞 Contact us now, let’s analyze your system.
Legal today, strong tomorrow.